
Protecting Yourself from Cybercrime Dangers: Harden Your Wireless & Bluetooth Connections and Use Public Wifi With Extreme Caution – AvoidAClaim: Claims Prevention & Practice Management for Lawyers
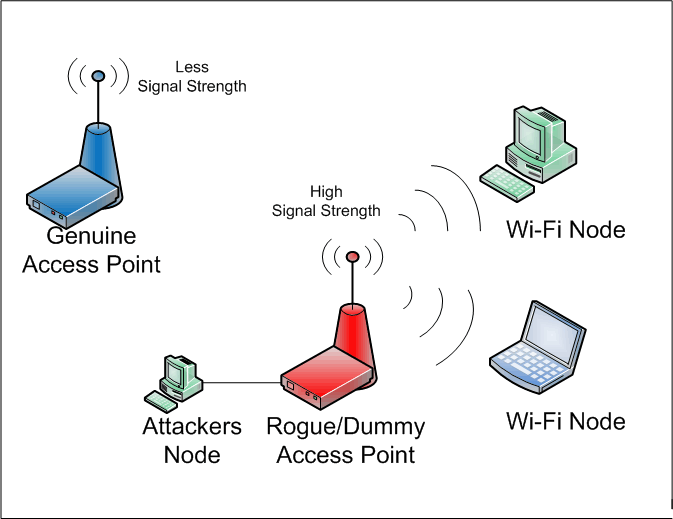
Network Security : WiFi Security fixation | Pune Mumbai Hyderabad Delhi Bangalore India | Valency Networks


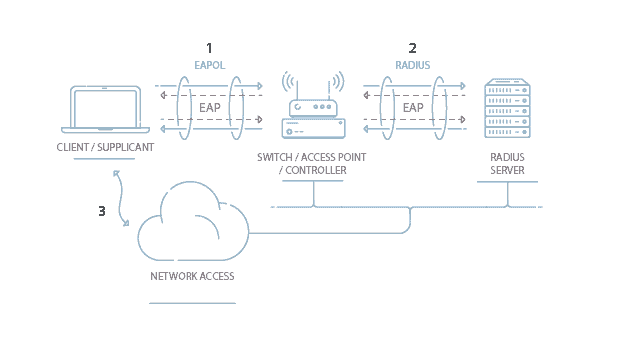

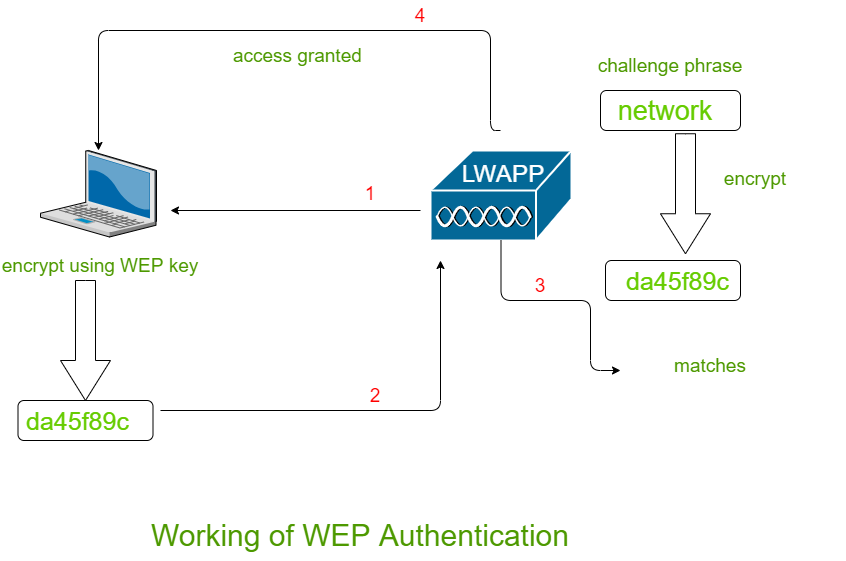


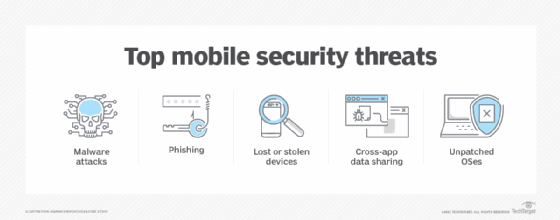









![PDF] Data security and privacy in wireless body area networks | Semantic Scholar PDF] Data security and privacy in wireless body area networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c16b8b3d65c8d49bbd7c4de0876186edf793fc2b/2-Figure1-1.png)





